How To Use SSL To Connect A Blocking Resource?
December 31, 2024 | by [email protected]
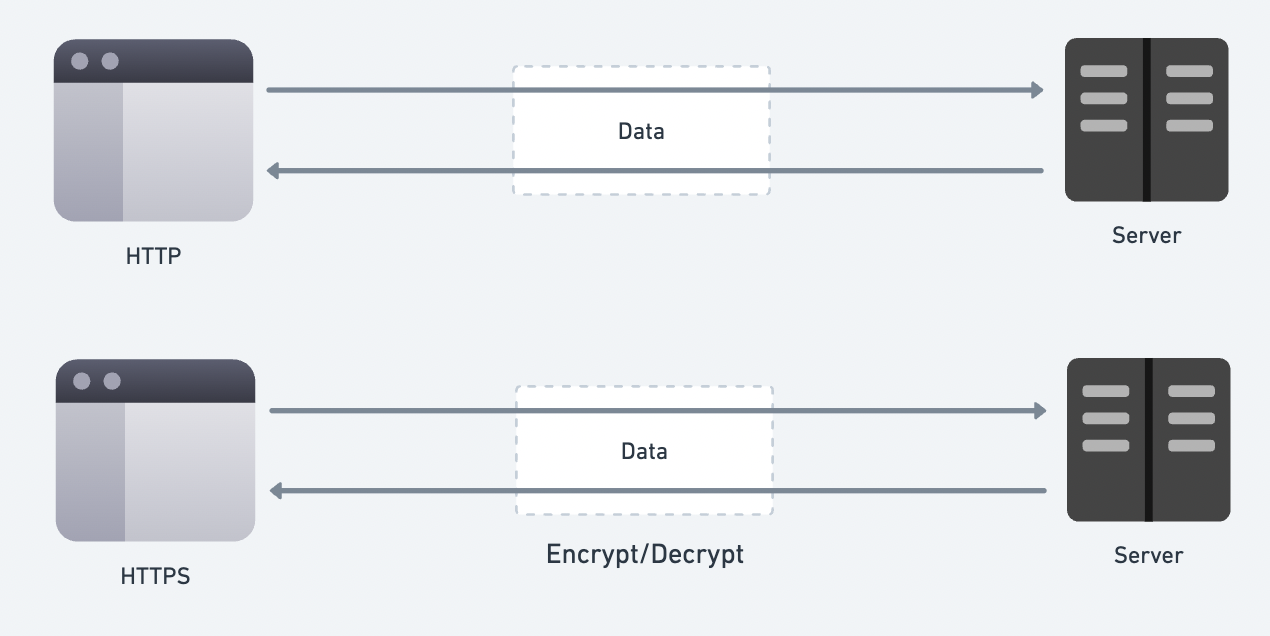
Problem
In some cases, you need to connect to resources hosted on servers that are protected by a firewall or located within a private network, making them inaccessible from the outside. Companies typically handle this situation using one of the following methods:
- Virtual Private Network (VPN)
- SSH Port Forwarding (Tunneling)
Local Port Forwarding with SSH
Local Port Forwarding is a common use case of SSH Port Forwarding, allowing you to connect to resources on a server protected by a firewall.
Scenario:
You have a Redis service running on a remote server at the port 6379. However, the server’s firewall blocks direct access to this port from outside the network. By using SSH Port Forwarding, you can securely connect to the Redis instance through an SSH tunnel.
Syntax:
ssh -L <local-port>:<remote-address>:<remote-port> <username>@<server-ip>
<local-port>: The local port on your machine to map the connection.<remote-address>: The address of the resource on the remote server (oftenlocalhostfor services bound to the loopback interface).<remote-port>: The port of the resource on the remote server.<username>: The SSH username to log into the remote server.<server-ip>: The IP address of the remote server.
Example:
Case 1: Using Full Syntax
If your server’s IP address is 172.168.21.112, username is ec2-user, and Redis is running on port 6379, the command would be:
ssh -L localhost:6379:localhost:6379 [email protected]
Case 2: Simplified Command
You can omit the localhost at the beginning:
ssh -L 6379:localhost:6379 [email protected]
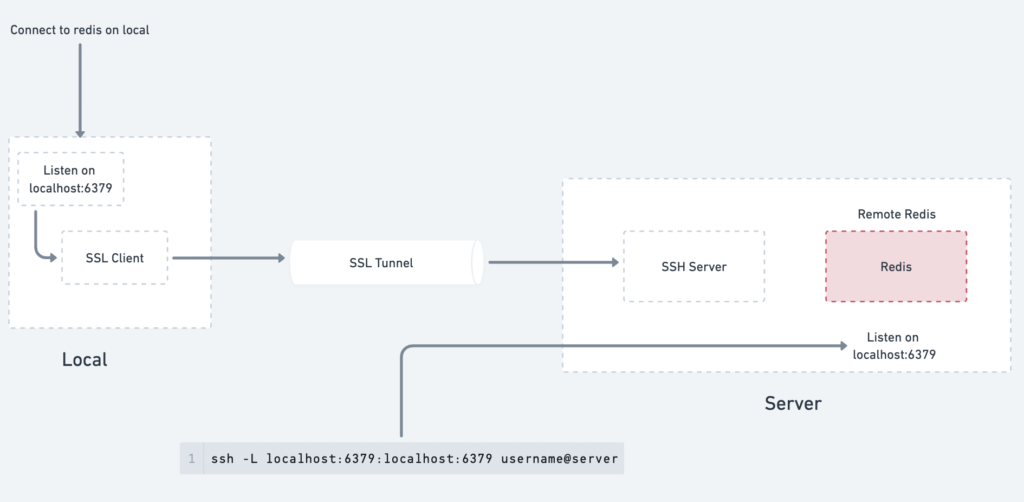
How It Works:
- SSH Tunnel: This command establishes an SSH connection to the server
172.168.21.112. - Port Mapping: It maps the local port
6379on your machine to the remote port6379of the Redis service running on the server. - Access Locally: After the tunnel is established, you can access the Redis service as if it’s running on your local machine:
redis-cli -h localhost -p 6379
Pros and Cons
Pros:
- Simple setup without requiring additional infrastructure.
- Ideal for accessing services directly protected by firewalls.
- No changes to the network configuration are needed.
Cons:
- Limited resources on a single server.
- Requires a direct SSH connection to the server.
- Not suitable for accessing resources inside a private network (e.g., VPC).
Bastion Host
SSH Port Forwarding to Access Resources in a Private Network
Another common use of SSH Port Forwarding is to connect to resources located in a Private Network, such as databases hosted on cloud services like AWS.
Scenario:
For instance, AWS Amazon Relational Database Service (RDS) instances are typically created in a private network (VPC) for security reasons, making them inaccessible from the outside. To connect to the RDS instance, a Bastion Host is often used as a secure entry point to the private network.
Syntax:
ssh -L <local-port>:<remote-address>:<remote-port> <username>@<bastion-host-ip>
<local-port>: The local port on your machine to map the connection.<remote-address>: The address of the resource inside the private network (e.g., the RDS endpoint).<remote-port>: The port of the resource (e.g., 3306 for Mysql).<username>: The SSH username to log into the bastion host.<bastion-host-ip>: The public IP address of the bastion host.
Example:
Case: Connecting to an RDS Instance via a Bastion Host
- Details:
- Bastion Host IP:
172.168.21.112 - Bastion Host Username:
ec2-user - RDS Endpoint:
mysql.123456789765.us-east-1.rds.amazonaws.com - RDS Port:
3306(Mysql default port)
- Bastion Host IP:
- Command:
ssh -L 3306:mysql.123456789765.us-east-1.rds.amazonaws.com:3306 [email protected]
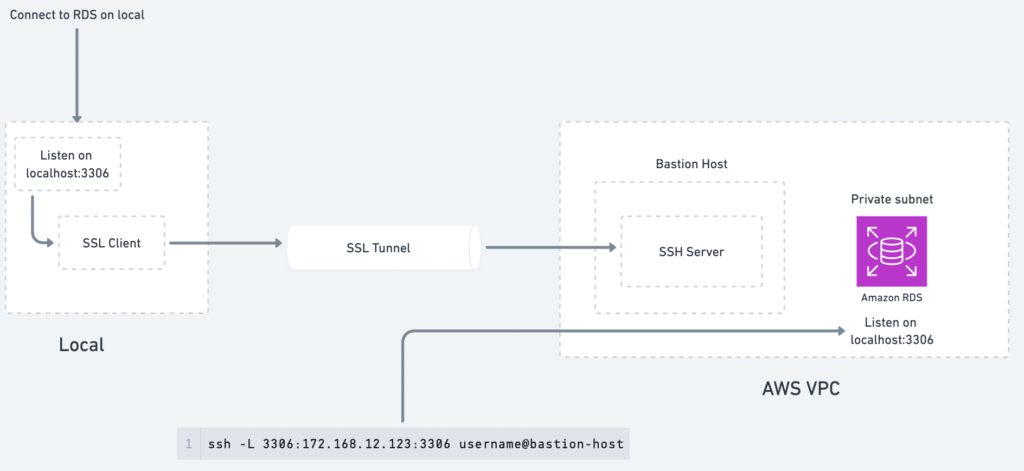
How It Works:
- SSH Tunnel: The command establishes an SSH connection to the Bastion Host (
172.168.).21.112 - Port Mapping: It maps the local port 3306 on your machine to the remote RDS instance’s port 3306 via the bastion host.
- Access Locally: You can now connect to the RDS instance using tools like
psqlor any database client as if it’s running locally:
psql -h localhost -p 3306 -U <username> -d <database>
Pros and Cons
Pros:
- Provides secure access to private network resources.
- Keeps private resources isolated from the public internet.
- Scales well for accessing multiple private resources.
Cons:
- Requires setting up and maintaining a bastion host.
- Configuration is slightly more complex than local port forwarding.
- May require multiple tunnels if accessing multiple resources on different ports.
Summary
SSH Port Forwarding allows secure access to private network resources, such as AWS RDS, through a bastion host by creating an encrypted tunnel. It maps a local port to the remote resource’s port, enabling seamless and secure connectivity without exposing the resource to the public internet.
References
RELATED POSTS
View all